Meow, Meow Leaks, and the Chaos of Ransomware Attribution

Meow has captivated the attention of cybersecurity and threat intelligence teams as a threat to watch in 2024. The group’s nebulous profile, rising victim count, and operational model make them a standout compared to other groups. Even more intriguing is the growing number of aliases that have been grouped with Meow, including Meow Leaks.
Meow or Meow Leaks?
Various cybersecurity firms have identified Meow as a significant threat. Meow is a ransomware group that emerged in 2022. Although many experts in the cybersecurity and incident response communities link Meow to the Meow Leaks entity, there is some debate on whether they are the same group operating under different aliases or two distinct entities with distinct operational models.
The Meow threat identified in 2022 is described as a ransomware group that targets organizations based in multiple countries, including the United States, the United Kingdom, Nigeria, and Italy. The ransomware often infects systems through vectors such as common known vulnerabilities and zero days. Once encryption occurs, the ransomware appends the .meow extension to files and adds a note that directs victims to correspond over email or message Telegram accounts meow2022 and meow123 for payment instructions.
Meow is classified as a variant within the Conti malware family. It emerged following the Conti source code leak with the groups BlueSky, ScareCrow, and Putin Team. This same Meow threat has also been referred to as Meow Corp and Meow2022. Meow operates based on the Ransomware as a Service (RaaS) model. In March of 2023 a decryptor was released that allowed victims to recover from Meow ransomware. This likely hampered the group’s operations.
Meow Leaks’ operations took shape in 2023. Meow Leaks has been characterized by multiple threat reporting outlets as a ransomware group. The tactics employed by Meow Leaks however differ from Meow. Meow Leaks conducts operations that typically result in the exfiltration of data rather than both encryption and exfiltration which was a pattern that was observed with Meow’s activities.
Meow Leaks Victimology
The victims of Meow Leaks include countries such as the United States, United Kingdom, Germany, and Japan; the group is also known for having a victim demographic that falls into a variety of sectors such as government, healthcare, education, technology, and finance. Meow Leaks emerged in August of 2023, with few attacks performed from the end of 2023 leading into 2024. In July of 2024, however, their attacks would see an exponential increase. This increase may be a result of an overestimation or miscalculation of alleged victims. It may also have emerged from Meow Leaks exchanging data leaks with other affiliate groups.
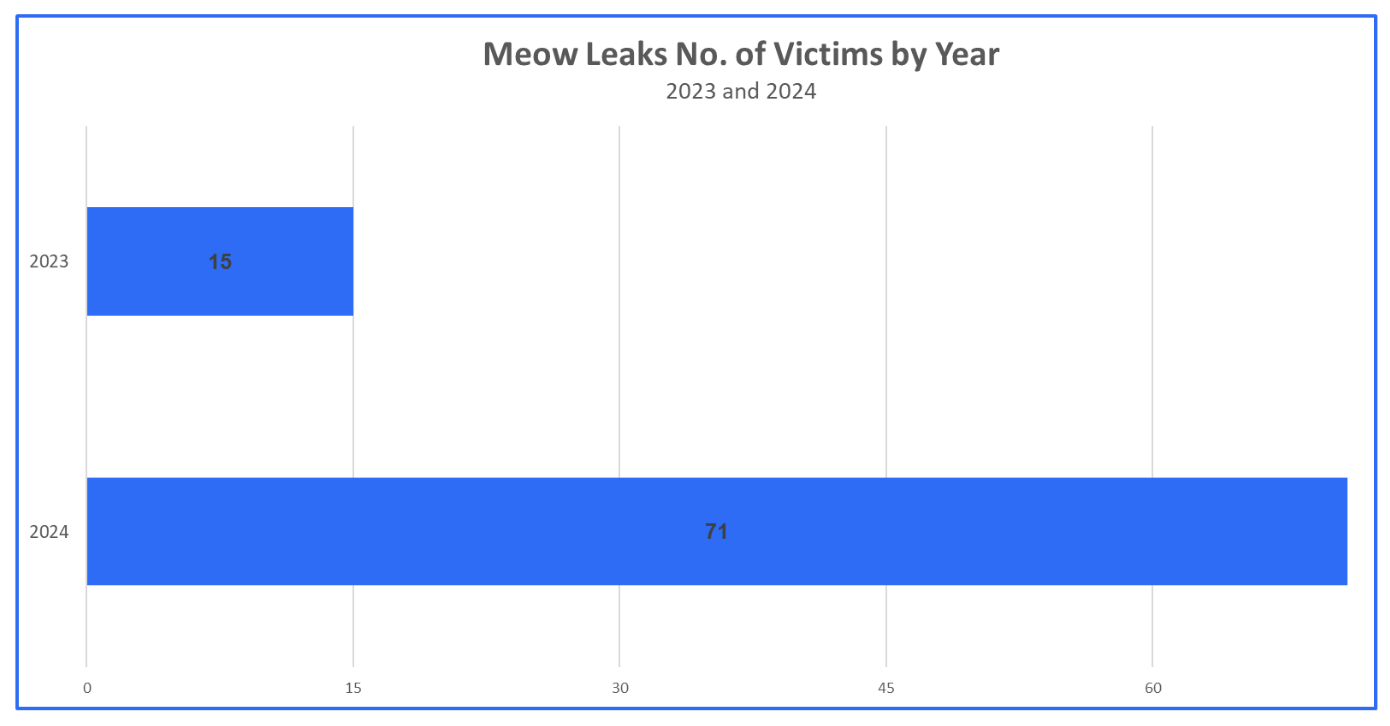
Figure 1: Meow Leaks victims in 2023 and 2024.
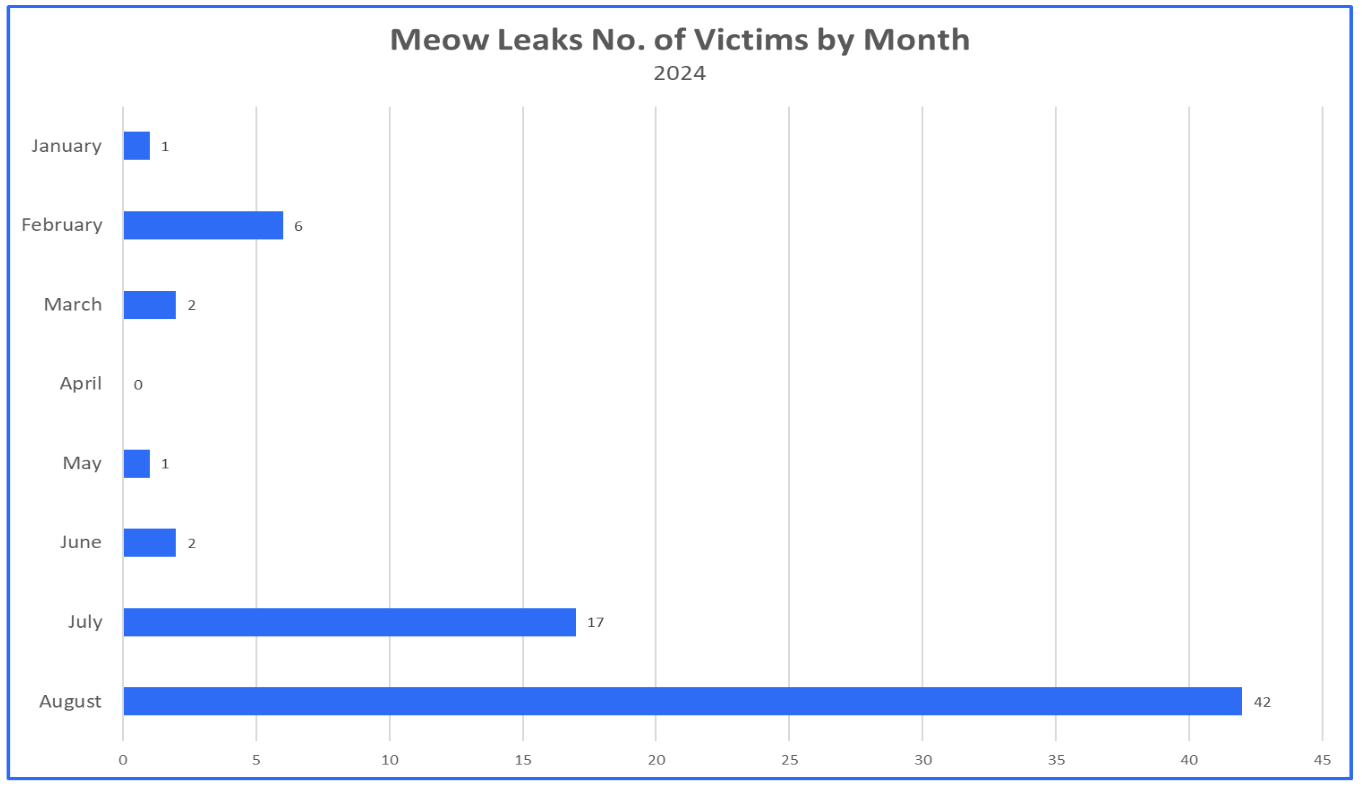
Figure 2: Meow Leaks victims by month in 2024.
The Shift in Ransomware Group Operational Goals
As early as 2016, it was common for ransomware groups to operate using the ransomware as a service (RaaS) model. Those groups started out with an objective to encrypt victim data so that the victim had no choice other than to pay for a decryption key. Ransomware groups then evolved to encrypt and exfiltrate data. Now, groups whose sole purpose is to exfiltrate data are becoming more and more prevalent.
The trend of ransomware groups moving away from encryption or double extortion methods to exfiltration may have manifested due to multiple factors that impact the cost and complexity of operations. Without a focus on encryptors, the costs associated with tooling and modifying code for an operation may be greatly reduced; this would allow funds to be invested in other areas or a greater percentage of earnings could go back into the operator’s budget.
It’s also worth noting that when selling data that’s acquired during exfiltration activities, the purchase price for that data alone might be more variable. This could result in more sales since the costs associated with accessing accounts, backup files, configurations, and other critical resources are taken out of the equation. There’s also less hassle for operators to wait or rely on victim communications and payments alone, as they have a wider reach.
Extortion Methods
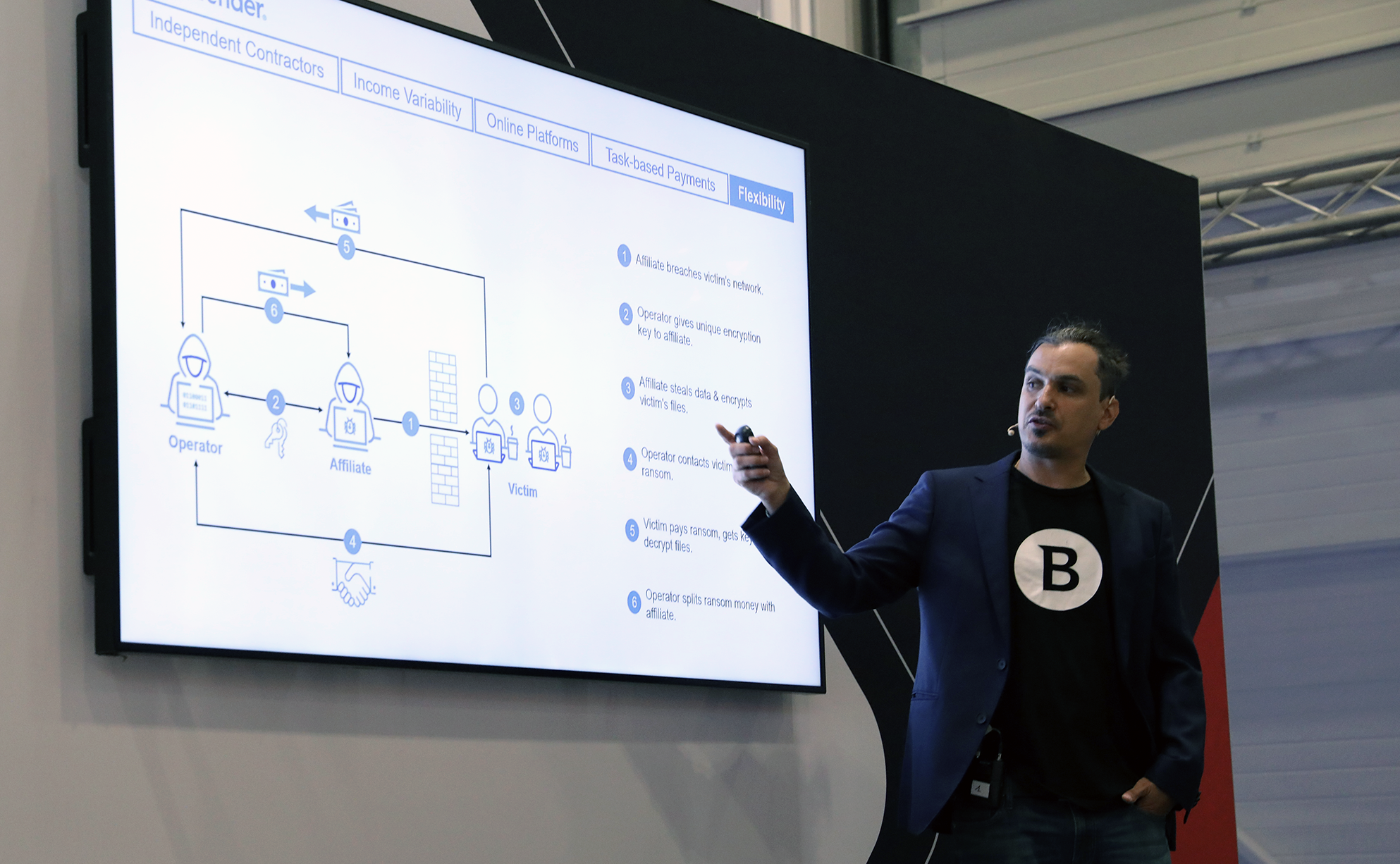
In a recent interview conducted by SuspectFile, Meow Leaks stated that they are not involved with Conti and have no affiliation with Meow Corp. While that is a curious statement, it’s also important to examine the different types of extortion that exist and determine how Meow Leaks operations may lean towards one in particular. A double extortion ransomware operation involves two main components: encryption and exfiltration. The double extortion cycle also incorporates threatening the release of sensitive data to pressure victims into making payments.
Meow Leaks is known for exfiltrating data, which is sold on a marketplace named Market Meow Leaks. This unauthorized access and/or disclosure of sensitive data indicates a breach of confidentiality. Meow Leaks is just one example of a group that has a primary goal to steal (exfiltrate) data.
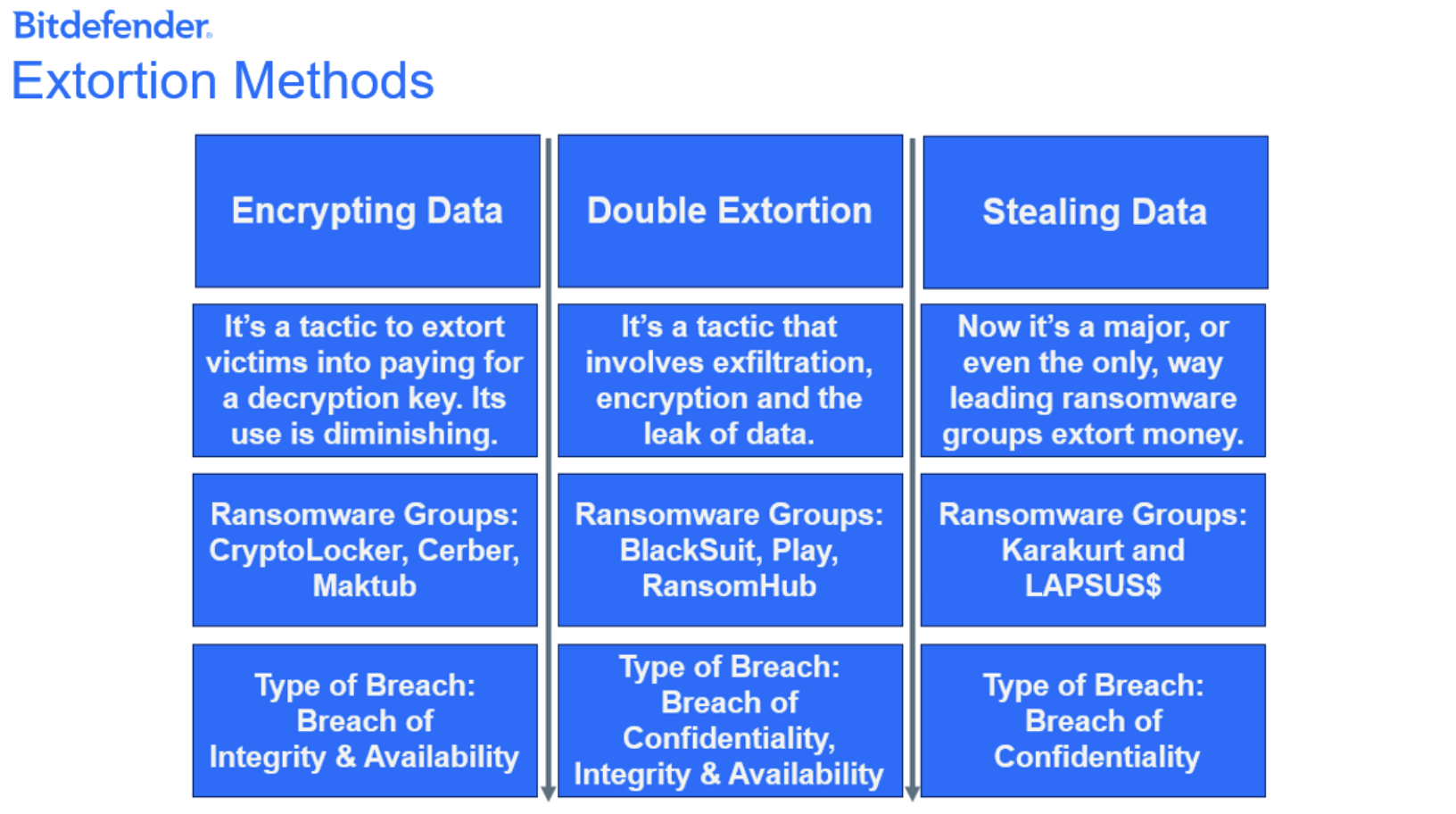
Figure 3: Extortion Methods
Some threat groups may employ single extortion or one extortion tactic, only to alter their operations to allow double extortion. It is important to note that Meow, like most other threat actors, could employ double extortion.
Attribution Considerations
The different types of extortion methods call attention to one way that is useful to categorize threat groups. Still, there is uncertainty about if Meow Leaks operates in a manner that lines up with their image. The Bitdefender SOC team reported that Meow Leaks emails victims with the following message:
Hello, we are the Meow team! We don't do viral ransomware and we don't want your company to be affected by it. But we do have your data that we may sell on the black market if we don't find a compromise. Please respond to this message as soon as possible, and we'll provide more information about the leak and help you close the vulnerabilities.
Sincerely, Meow Leaks.
We invite you to check out our website to start the conversation!
This type of messaging is significant for threat management teams and security researchers. It raises questions about whether Meow Leaks’ operations are independent of another threat group and do not involve ransomware as they claim.
Bitdefender’s SOC team also theorized that Meow Leaks works within a small group and most likely has fewer staff and technical resources available compared to other prolific threat groups. The result of many Meow Leaks attacks reported in 2024 is data exfiltration. Meow Leaks sells victim data on their marketplace known as Market Meow Leaks. With exfiltration and the marketing of that data taking priority, this may explain why limited reports documenting system compromise would be available.
The Market Meow Leaks Website
Market Meow Leaks is accessed via Tor. Meow Leaks does not demand a payment to prevent data exposure or restore system access into their operational model. So, there is no note that mentions access to a sample decryption key and no there is no countdown to identify when a data leak will occur.
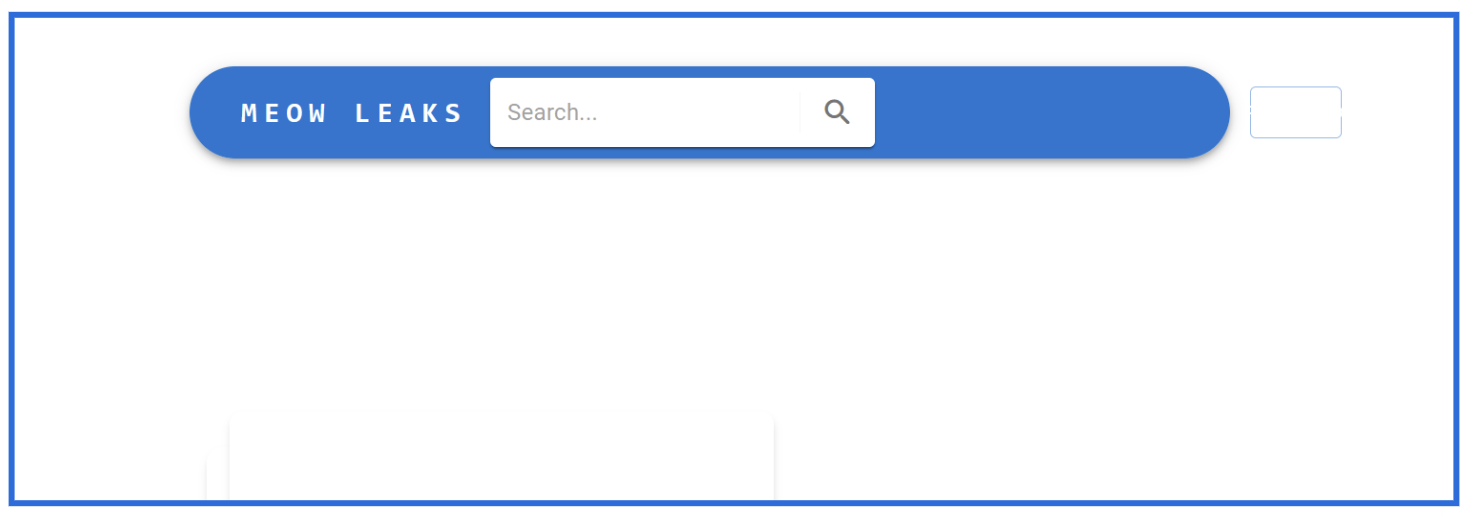
Figure 4: Market Meow Leaks website.
On Market Meow Leaks, data leaks are sold so they can be available to multiple parties. As a result, the data leaks are intended to reach a wider population that extends beyond victim organizations. Buyers have the option to either purchase the leaked data ‘in one hands’ or ‘in several hands.’ Preview images on the data leak pages feature documents and, in some circumstances, chats initiated by the victim. Customers are prompted to contact a representative, selecting from the platforms Jabber, TOX, or Matrix and providing their username for future correspondence. There is also a feedback submission area that allows users to submit questions or other content and provide a contact email address. No Telegram channel has been traced back to Meow Leaks.
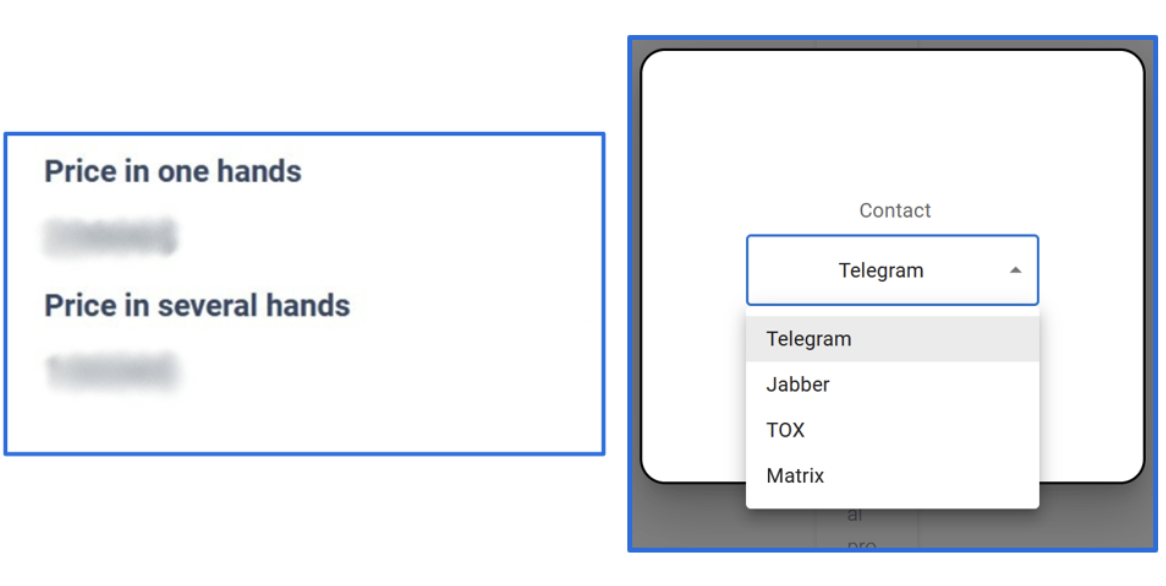
Figure 5: One or multiple buyer options or contact platforms.
Marketplace Information and Data Leak Sources
Unlike other well-known groups, Meow Leaks does not offer information on their marketplace site to indicate which data leaks are paid off. And there is no forum to react to data leak content. The number of views for each data appears as the only detail on potential interactions. Price reductions are also displayed on some leak pages. Whether those price reductions are a sales ploy or reflect the quality of the leak, leak size, or length of time since the leak transpired remains unknown.
While Meow Leaks has appeared in reports that document attacks against victim organizations, since the group runs a marketplace, it is unclear how much of their operations are sustained by planned cyberattacks, and how much of their operations stem from data leaks purchased or acquired elsewhere. This makes drawing a precise picture of their impact and resources difficult.
An Old Site: meowleaks.org
Excluding the Marketplace Meow Leaks site, there is a website called meowleaks.org that dates to 2023. The site explicitly mentions both Meow Leaks and the phrase leaker and is considered an older blog site.
The meowleaks.org site does not feature purchase links or data leak content. It does however indicate potential victims in government, education, and healthcare and their presence around the country. There is also a code of ethics or what appears to be rules of engagement for how they operate, including only leaking true and accurate information and valuing a just society. While it was reported in July of 2024 that Market Meow Leaks is a redesign of a former web site, it is unknown if its administrator also manages the meowleaks.org site.
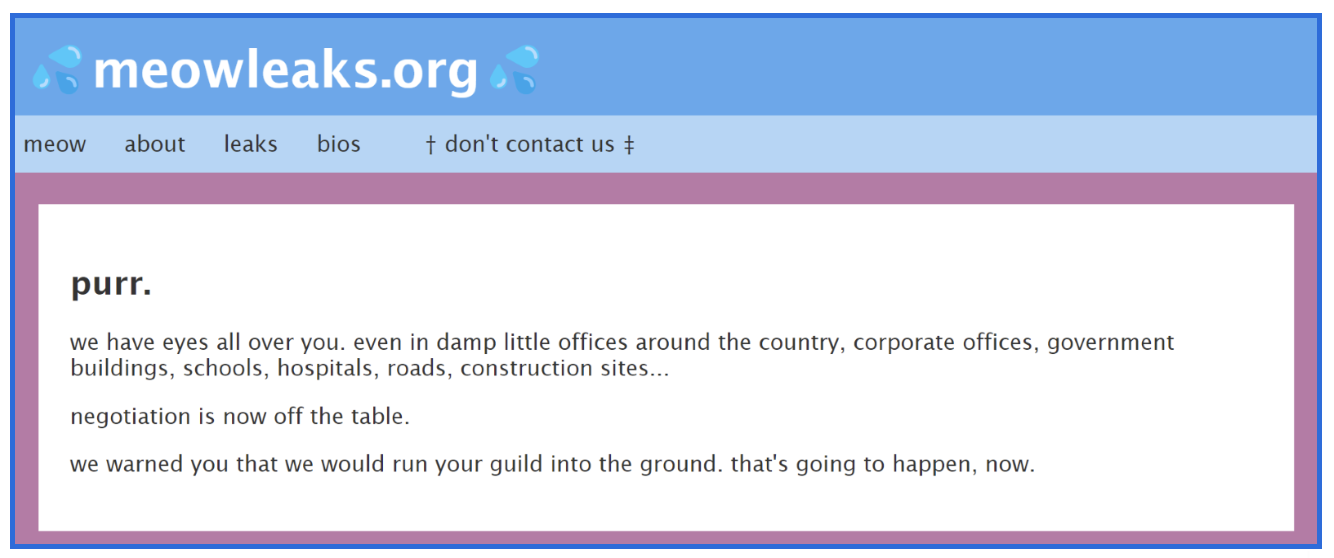
Figure 6: meowleaks.org home page.
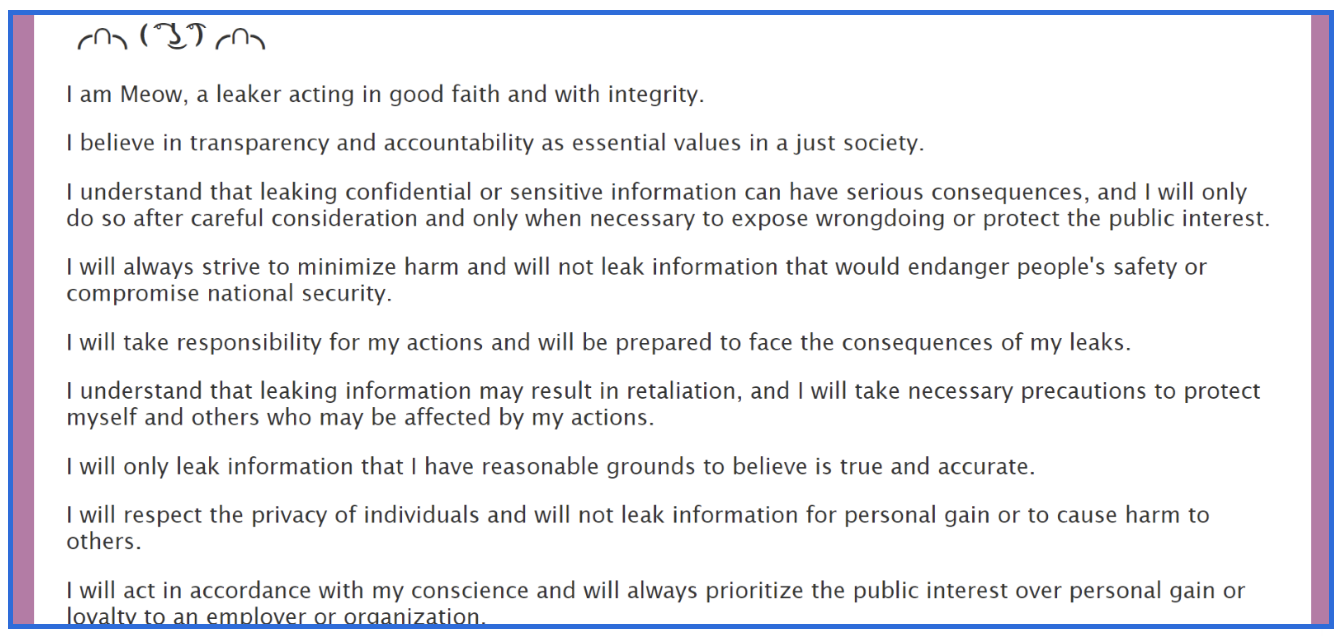
Figure 7: meowleaks.org site.
The meowleaks.org ‘Bios’ tab features a Blizzard link that directs users to the Meow Meow Kitties, also referred to as MMK, guild profile. The Meow Meow Kitties guild was established in 2021. While the guild profile specifically has not been updated in over a year, the guild remains active, with members unlocking achievements as recently September of this year.
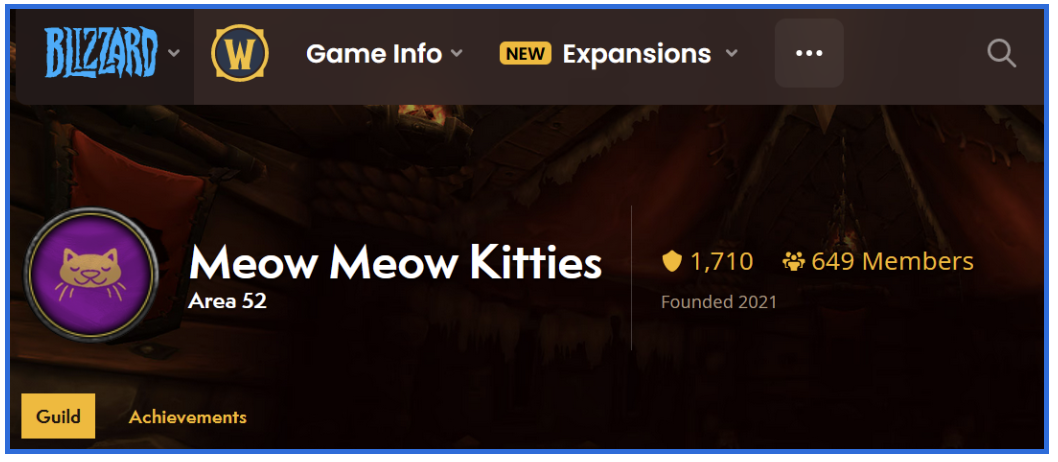
Figure 8: Meow Meow Kitties World of Warcraft Guild.
The guild is not accessible to World of Warcraft players who have not met several conditions for joining. This may have initially been a tactic to weed out casual gamers from veterans or to prevent undesirable candidates from joining.
Players hoping to submit an application to join the Meow Meow Kitties guild must submit an application that validates their BattleNet stats. The stats would show that the applicant has a World of Warcraft character established in the Americas region of the retail version of the game that is at least level 70, with an item level of at least 460.
While character boost or upgrade purchase options are available to increase character levels, item levels may only be increased by completing certain quests or live game rounds. Since Telegram, Jabber, TOX, etc. are in use on the newer Market Meow Leaks site, it is less likely that Meow Leaks members will want to engage solely through World of Warcraft.
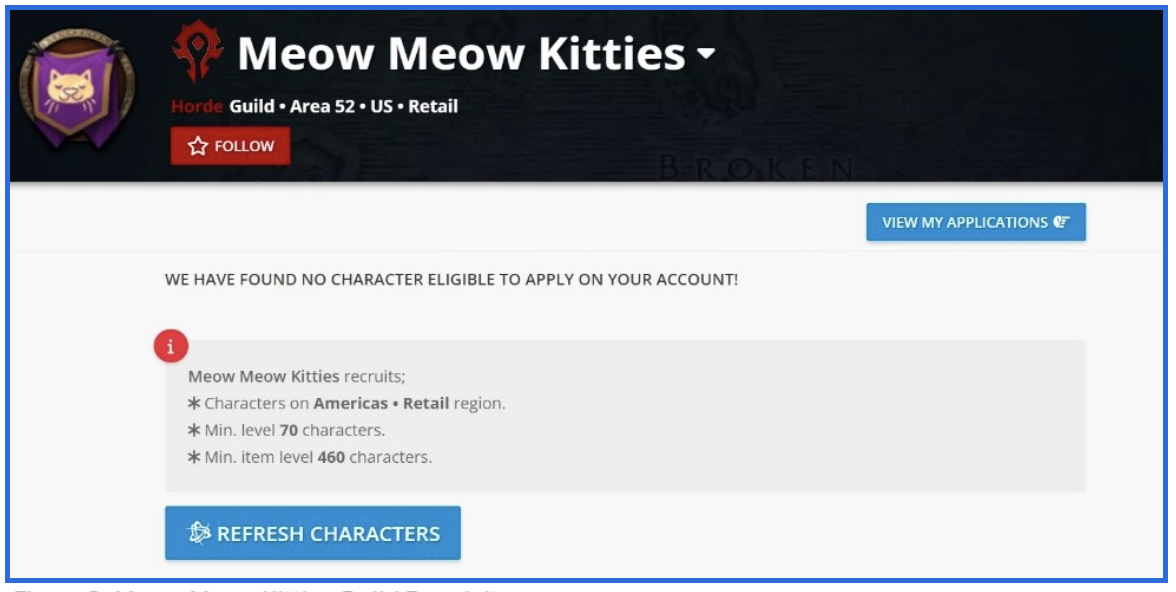
Figure 9: Meow Meow Kitties Guild Requisites.
Tactics, Techniques, and Procedures
There are several questions surrounding what Meow Leaks is capable of and whether their attacks involve both system compromise and data theft. In a recent incident analysis conducted by Bitdefender’s SOC team and supported by the CTI team, several instances were observed which may shed light on prior claims about Meow Leaks.
Initial Access
During a Meow Leaks incident analysis performed by Bitdefender, the use of both phishing emails and malvertising were observed. A phishing instance resulted in users clicking on a link to initiate a download, launching a malicious executable or installer in the process.
Exploitation and Lateral Movement
Meow Leaks has been identified as a threat actor that uses customized scripts to gather further information on targets and to establish persistence, Bitdefender noted in their analysis that Python scripts have been used by Meow to launch exploits and attempt to establish connections to remote hosts. Scanner tools like NetScan were also at the threat actor’s disposal to map out the victim network and establish lateral movement.
Execution
While Meow Leaks has stated that they do not handle ransomware, in a recent Meow incident analysis conducted by Bitdefender, a ransomware encryptor was identified. It was associated with a windows.exe process that was not managed by a victim host. This use of an encryptor suggests that Meow Leaks is open to using ransomware.
Exfiltration
Bitdefender stated that Meow Leaks was observed adding a MegaSync executable to a local account on a victim system. MegaSync, a cloud storage client, was likely the application used for exfiltration.
Persistence
PowerTool32.exe and PowerTool64.exe were identified as resources the Meow Leaks attacker had available to infiltrate and modify processes in the kernel space of a target and to conceal malicious activities. Spoolsv.exe was also identified as a potential persistence technique; the malicious executable was accessed from a shared folder associated with the attacker.
Defense Evasion
Bitdefender noted that the Meow Leaks attacker attempted to create the file called truenight.sys. That system file, known for interacting with actions at the kernel-level can kill EDR processes.
Recommendations
There are multilayered strategies that an organization can implement to help guard against a ransomware attack. An organization may incorporate best practices into their security program to address gaps in Prevention, Protection, Detection, and Response security measures. The recommendations included below are instrumental for an organization aiming to mitigate and minimize the impact of ransomware threats.
1. Establish Data Recovery and Resiliency practices: Schedule frequent backups; doing so is important as it ensures that critical data and systems can be restored if a compromise occurs. It’s advised that backups are stored in an offline location and/or cloud environment that is kept separate from the main network. Also, ensuring that backups are regularly tested is essential to verify that no issues impacting data integrity are present.
2. Implement Security Awareness and Training: Establish regular cybersecurity awareness training that focuses on identifying and reporting instances of phishing and social engineering. Teach employees how to recognize suspicious emails, links, and attachments that may be employed to deliver malicious payloads.
3. Implement Email Security Solutions: Use email filtering solutions to block malicious emails, attachments, and links Add further protection by enabling attachment sandboxing; this allows a scan to run in real time, proactively identifying ransomware contained in attachments before the attachment is delivered to a user. Disable macros in Microsoft Office documents by default to eliminate opportunities for an attacker to use macros to deliver ransomware payloads.
4. Perform Patch Management: Regularly patch and deploy updates across all software, operating systems, and applications. Ensure critical updates are applied promptly, particularly for vulnerable remote access systems such as VPNs, RDP, and firewalls.
5. Implement Endpoint Detection and Response Solutions: Deploy advanced endpoint protection (EDR) solutions to detect and block ransomware. Use EDR technologies that leverage both behavioral and heuristic-based detections to ensure that initial infection vectors are accurately detected and escalated for investigation. Enable real-time threat detection and automated responses to allow actions that result in isolating compromised devices or blocking malicious processes.
6. Execute an Incident Response Plan that supports rapid response: Maintain a mature incident response process to support rapid response actions. Rapid response is a vital part of ransomware mitigation and time cannot be wasted during incident response actions. Ensure that the security team has the people, processes, and technologies in place to properly investigate and respond to an incident, e.g. blocking IPs, stopping processes, or isolating hosts to cut off an attacker’s access to critical data and resources and preventing further exploitation.
7. Leverage Advanced Threat Intelligence: The right threat intelligence solutions can provide critical insights about attacks. Bitdefender IntelliZone is a solution that consolidates all the knowledge we've gathered regarding cyber threats and the associated threat actors into a single pane of glass for the security analysts, including access to Bitdefender’s next-generation malware analysis service. If you already have an IntelliZone account, you can find additional structured information about Meow under Threat IDs that include: BDvqk73mkz, BD5i0sjstn, BDo40swk73, BDhciojbkr, BDq1kv7y38, BDhkzy743q.
8. Implement Network Protection controls like Network Attack Defense and network segmentation: Segment networks to limit lateral movement if an endpoint is compromised. Implement least-privilege access controls, restricting who can access critical systems.
9. Secure Remote Access: Enforce multi-factor authentication (MFA) for all remote access points, including VPNs and RDP. Use a VPN or secure access gateway for remote users instead of exposing RDP directly to the Internet.
10. Disable Unessential Services and Ports: Disable unused ports and services to reduce potential attack vectors. Continuously monitor and evaluate unauthorized services running in the environment.
11. Implement File Integrity Monitoring: Use file integrity monitoring (FIM) to detect unauthorized changes in system files, which can indicate ransomware encryption activity.
12. Incorporate a Data Loss Prevention (DLP) into your Security Protection and Prevention strategy:Deploy a DLP solution to monitor, detect, and block unauthorized transfers of sensitive data, reducing the risk of data exfiltration during ransomware attacks.
Indicators of Compromise
In recent months, several organizations have reported on IOCs for the group Meow. Whether Meow can be considered separate from Meow Leaks is a topic that merits further research. Meow Leaks is currently identified as an alias for Meow; a subset of their IOCs is included below:
Indicators of Compromise
| IP Addresses |
|---|
|
95.164.69.179 |
| SHA-256 |
|---|
|
222e2b91f5becea8c7c05883e4a58796a1f68628fbb0852b533fed08d8e9b853 |
|
7f6421cdf6355edfdcbddadd26bcdfbf984def301df3c6c03d71af8e30bb781f |
|
513c18df31e04137e97b90bdc36da10bf2cb1036f0911ab14ab46fc630149ca4 |
|
fe311979cd099677b1fd7c5b2008aed000f0e38d58eb3bfd30d04444476416f9 |
|
7f624cfb74685effcb325206b428db2be8ac6cce7b72b3edebbe8e310a645099 |
|
5a936250411bf5709a888db54680c131e9c0f40ff4ff04db4aeda5443481922f |
|
b5b105751a2bf965a6b78eeff100fe4c75282ad6f37f98b9adcd15d8c64283ec |
| SHA-1 |
|---|
|
85147575c1a6f57d849747dfd8293e9a |
We would like to thank the Bitdefenders Ovidiu Ardelean, Joshua Armstrong, Tyler Baker, Paul Lupo, and Sean Nikkel (sorted alphabetically) for their support throughout the blog’s development.
tags
Author

Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks