Hello, now 2 times via extended threat detection a PS ****** was stopped. Dont now the real origin/executer, but virustotal said 0 found malicious, also their sandboxes, even Bitdefender…
Then I only could screencopy the finding, no text copy/rightklick, no button to a logfile. :/ so I used chatgpt for OCR. Later I found only under notification I can mark text and copy via rightclick. Seems like a hidden feature..
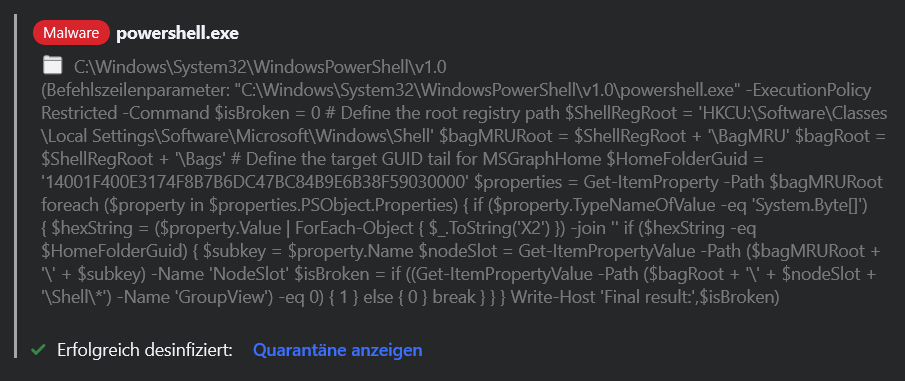
Finding (copy then has no line breaks :/ like in GUI):
Funktion:Erweiterte GefahrenabwehrDie Anwendung powershell.exe wurde als potenziell schädlich erkannt und blockiert.Anwendungspfad: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exeBefehlszeilenparameter: "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Restricted -Command $isBroken = 0 # Define the root registry path $ShellRegRoot = 'HKCU:\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell' $bagMRURoot = $ShellRegRoot + '\BagMRU' $bagRoot = $ShellRegRoot + '\Bags' # Define the target GUID tail for MSGraphHome $HomeFolderGuid = '14001F400E3174F8B7B6DC47BC84B9E6B38F59030000' $properties = Get-ItemProperty -Path $bagMRURoot foreach ($property in $properties.PSObject.Properties) { if ($property.TypeNameOfValue -eq 'System.Byte[]') { $hexString = ($property.Value | ForEach-Object { $_.ToString('X2') }) -join '' if ($hexString -eq $HomeFolderGuid) { $subkey = $property.Name $nodeSlot = Get-ItemPropertyValue -Path ($bagMRURoot + '\' + $subkey) -Name 'NodeSlot' $isBroken = if ((Get-ItemPropertyValue -Path ($bagRoot + '\' + $nodeSlot + '\Shell\*') -Name 'GroupView') -eq 0) { 1 } else { 0 } break } } } Write-Host 'Final result:',$isBrokenErkennungs-ID: SuspiciousBehavior.2304F2F54F048A90