Concerning: : Windows XP/Vista/7, Firefox 8 (with plugins Java Deployment Toolkit and Java Platform enabled), Java 6u26 up to ???
Risc level: very high (executes binary code with user rights)
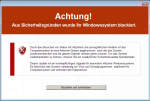
Customers have reported me an windows system virus infection. Every time the infected system is booting with web access, the desktop is blanked out. Just an 'always on top' screen arises with a pretended security alert and the ‘service offer’ to remove security issues for a payment of 50 EUR. No chance to close it or access the task manager.
The warning message in german:
“Achtung! Aus Sicherheitsgründen wurde Ihr Windowssystem blockiert.
Durch das Besuchen von Seiten mit infiziertem und pornografischen Inhalten ist das Computersystem an eine kritische Grenze angekommen, nach der das System zusammenbrechen und die ganzen Dateien verloren gehen können. Um das System wiederherstellen zu können, müssen Sie ein zusätzliches Sicherheitsupdate herunterladen. […]”

I analyzed the infected machines and the virus in a virtual machine.
The malware source is (OPEN AT YOUR OWN RISC!):
http://macbookc.in/main.php?page=aeb8ca92008321ee
Possible infection mechanism:
The embedded (JavaScript) code starts the firefox plugin-container for java and provokes a crash. While firefox crash reporting or java deploying system is working the malware code (deposited in AppData\LocalLow\Sun\Java\Deployment\*) is being executed with user account rights:
"<firefox portable path>\App\firefox\plugin-container.exe" --channel=3576.3863a60.1498215984 "…\Java\jre6\bin\new_plugin\npdeployJava1.dll" - - greomni "<firefox portable path>\App\firefox\omni.jar" 3576 "\\.\pipe\gecko-crash-server-pipe.3576" plugin"
then:
"…\Java\jre6\bin\java.exe -D__jvm_launched=219932753 -Xbootclasspath/a:C:\PROGRA~1\Java\jre6\lib\deploy.jar;…\Java\jre6\lib\javaws.jar;…\Java\jre6\lib\plugin.jar -Djava.class.path=…\Java\jre6\classes -Dsun.awt.warmup=true sun.plugin2.main.client.PluginMain write_pipe_name=jpi2_pid3060_pipe2,read_pipe_name=jpi2_pid3060_pipe1"
A new created registry entry in the USERS auto start refers to a newly created file “hostrun.exe”
Registry entry:
[HKEY_USERS\<xxxxx>\Software\Microsoft\Windows\CurrentVersion\Run]
"{…}"="C:\\Users\\<USER>\\AppData\\Roaming\\Microsoft\\hostrun.exe"
Probably the windows updating system has been corrupted by locking or destroying the catdb-file (located in <winroot>\system32\catroot2\...\).
My suggestions:
Prevention:
- just visit serious websites (avoid warez and ****** stuff)
- use up-to-date plugins and java versions (exploit propably fixed in Java6u29)
- deactivate all unnecessary plugins in firefox.
Crisis management for infected systems:
Scan and rescue personal data both with an independent clean system (e.g. a separate machine and attached old disk) and reinstall the OS!
Feedback & experiences are welcome!
Kind regards
Arne Kostulski